John the Ripper Detect Hash Type
John has a built-in feature to detect what type of has its been given. John is fast and supports various cracking modes.

John The Ripper Pentesting Tool For Offline Password Cracking To Detect Weak Passwords Cyber Security
John-the-ripper MD5hash --formatRaw-SHA1-ng Using default input encoding.

. Its primary purpose is to detect weak Unix passwords. UTF-8 Loaded 1 password hash Raw-SHA1-AxCrypt SHA1 128128 SSE2 4x Press q or Ctrl-C to abort almost any other key for status 0g 0000003 33. Hashcat -a 0 -m 0 -O hash_string usrlibrockyoutxt.
Im working through an exercise that requires me to use john the ripper to crack a hash. Lets see how we use it. Allows you to override the hash type detection.
Identify and detect unknown hashes using this tool. John the Ripper is different from tools like Hydra. Identify the different types of hashes used to encrypt data positional arguments.
Cracking password in Kali Linux using John the Ripper is very straight forward. This page will tell you what type of hash a given string is. Now we have enough knowledge of the John the Ripper tool and we also installed it.
JtR detects the encryption on the hashed data and next if compares it with a large text file that contains popular passwords checks each. John The Ripper. Take for example the following hash altered to protect the google dork.
To get setup well need some. Include all possibilities expert mode Submit Identify. Copy the hash inside the text file and navigate to Hash Type Identifier Identify unknown hashes.
Its primary purpose is to detect weak Unix passwords. John is a great tool because its free fast and can do both wordlist style attacks and brute force attacks. Besides several crypt3 password hash types most commonly found on various Unix systems supported out of the box are Windows LM hashes plus lots of other hashes and ciphers in the community.
The tool we are going to use to do our password hashing in this post is called John the Ripper. The password of the archive zip is midnight. To do this we use the following syntax.
John --wordlistwordlist path to file Where--wordlistwordlist - specifies using wordlist mode and the file. My issue is john seems to like a hash file which is what I created i just threw the hash into a text file and john worked fine but my question is is it possible to just input a. John single formatraw-sha256 hashestxt.
Give it few seconds to detect the type of hash and crack the password. John the ripper and a raw hash. It supports a lot of encryption technologies unix encrypt 3 des sha-encrypt hashes etc for Unix and Windows based systems.
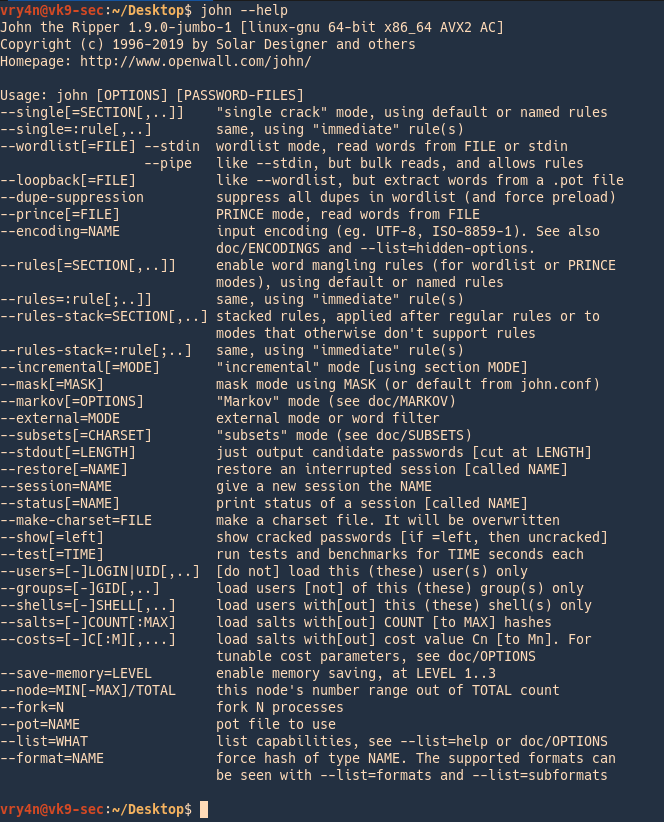
You can see it has already been identified the hash is WinZip and also other details like encryption Sha-1 algorithm. Hydra does blind brute-forcing by trying usernamepassword combinations on a service daemon like ftp server or telnet server. As of John the Ripper version 180 valid format names are descrypt bsdicrypt md5crypt bcrypt LM AFS tripcode dummy and crypt and many more are added in jumbo.
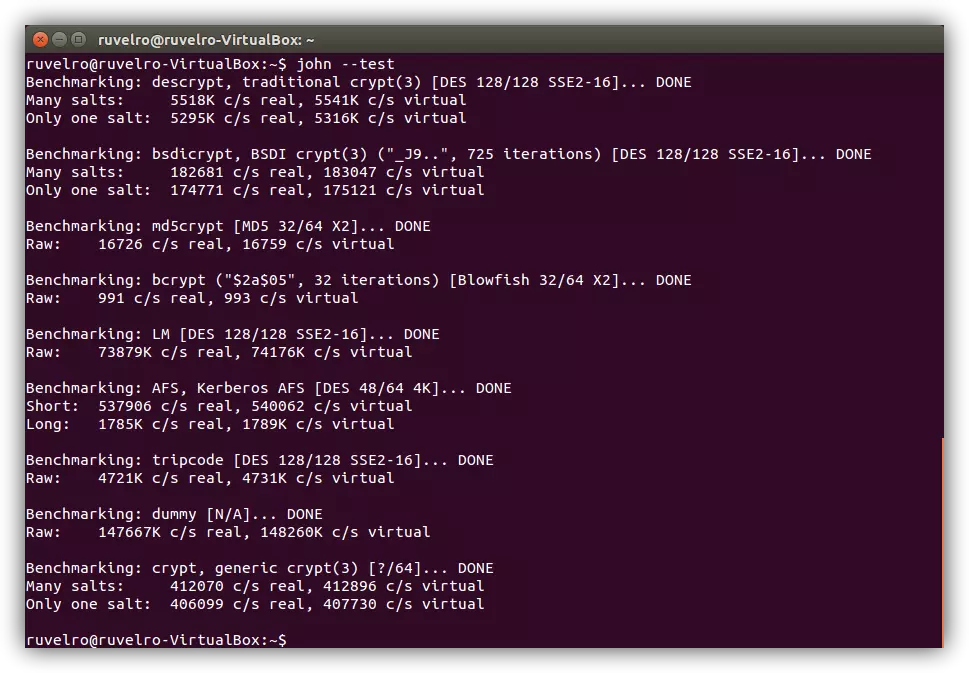
-e --extended list all possible hash algorithms including salted passwords -m --mode show corresponding Hashcat mode in output -j --john show corresponding JohnTheRipper format in output -h --help show this help message and. John the Ripper is one of the most used and popular password cracking tools. John the Ripper is a fast password cracker currently available for many flavors of Unix Windows DOS BeOS and OpenVMS.
To have JtR Pro or a -jumbo version focus on NTLM hashes. John the Ripper is a fast password cracker currently available for many flavors of Unix Windows DOS and OpenVMS. To force John to crack those same hashes again remove the johnpot file.
It also has the ability to auto-detect the hash type. Using this password cracker tool is very easy and straightforward you just need to type john followed by the hash file that you want to crack and then just define the format of the hash and hit enter. With PWDUMP-format files John focuses on LM rather than NTLM hashes by default and it might not load any hashes at all if there are no LM hashes to crack.
Path to file - file containing the hash you are trying to crack. Besides several crypt3 password hash types most commonly found on various Unix systems supported out of the box are Windows LM hashes plus lots of other. John --wordlist1000000-password-secliststxt hash John The Ripper command to break zip password.
The hash isnt in a file its just raw text. 44 What is the cracked value of hash2txt. John --listformats grep -iF sha1 Type in the following command and the answer will reveal itself.
To display cracked passwords use john --show on your password hash files. INPUT input to analyze default. Some tools make a educated guess regarding the encryption and salt type but there are numerous types of encryption schemes some so closely related that the hashes nearly looks the same.
Detected hash type sha512crypt but the string is also recognized as sha512crypt-cuda Use the --formatsha512crypt-cuda option to force. --single - This flag lets john know you want to use the single hash cracking mode. John the ripper craked it within a few minutes but hashcat never managed to crack it.
My password is trumpette. John has built-in features to detect what type of hash it is given and to select appropriate rules and formats to crack it for you. Lets assume we now have the hash and we have identified what type it is.
In this post I will demonstrate that. 43 What type of hash is hash2txt. As a newbie that registered in a network security class I was asked to hash MD5 a password and to crack it with hashcat.
Note that John cant crack hashes of. Now you can use unzip or 7zip. UTF-8 No password hashes loaded see FAQ john-the-ripper MD5hash --formatRaw-SHA1-Axcrypt Using default input encoding.
If you want to attempt to Decrypt them click this link instead. You can use this option when youre starting a cracking session or along with one of. If I ask a classic such as John the Ripper.
John options path to file john invokes the John the ripper program path to file The file contains the hash youre trying to crack. John however needs the hash first. Basic Syntax for John the Ripper commands.
Sudo john shadow Warning. Detected hash type sha512crypt but the string is also recognized as sha512crypt-opencl Use the --formatsha512crypt-opencl option to force loading these as that type instead Warning. To find the correct syntax for the command type in.
In this recipe we will see how to crack hashes with John the ripper. That is you normally only need to use --format when John would otherwise misdetect your hashcipher type eg when it says LM and you know that your hashes are in fact raw MD5 youd use --formatraw-md5 with -jumbo or if it would load undesired entries from the file. A brute force attack is where the program will cycle through every possible character combination until it has found a match.

John The Ripper Pro Password Cracker For Linux Distributor Reseller Resmi Software Original Jual Harga Murah Di Jakarta Melayani Se Indonesia
Crack Passwords Quickly Using John The Ripper
Cracking Password In Kali Linux Using John The Ripper Blackmore Ops

Basics Of John The Ripper Hash Testing Tool Tryhackme Complete Beginner Youtube

John The Ripper Fast Password Cracker Cyberpunk
Crack Windows Password With John The Ripper By Daniel Webimprints Medium

No comments for "John the Ripper Detect Hash Type"
Post a Comment